Along with the rapid development of network technology and the many computer connected in the world today, the increase in the crime world mayapun continue to happen. This is because more and more computer users interconnected via the internet. With the trend of increasing crime in the world virtual moment, then takes a security mechanism to the system of attacks from the hackers system (hackers) or from virus attack and other software that are considered dangerous to the workings of a system computer networks in both local and internet.
To find out how the hackers computer systems can do action against a target computer, it is necessary to know what tools used by hackers so that by knowing the workings of the tools it then can be made an appropriate security mechanism.
Nmap
Nmap is a utility to explore and audits of the system computer security. Nmap is free and available as open source code (open source code) that can be used under license from the GNU General Public License (GPL)
Nmap is a major project to make computer networks more secure and provide facilities / equipment for more sophisticated network security auditor computer and network administrators in the data exploration in managed computer network. Nmap is designed quite capable of doing quickly scan the process of large-scale computer networks and to a host for security, audit process, and exploration of computer networks.
How it works using Nmap packages Internet Protocol (IP) for determine the host / computer anywhere in the network active status is, what services are run by the host, any operating system used by the host, and type "packet filter" or whatever firewall used by the hosts in the network scanned by Nmap
at that time.
Figure 1 above is an example of Nmap display, which runs through command line. This example shows Nmap scan results showing TCP ports used by the target computer.
Nmap has 3 (three) main functions, namely: detection of the operating system, scan the port, ping scans. By default, Nmap doing a ping scan process to ping to each host to ensure the host is active or not. Some methods can be used, including sweeps of the Internet Control Messaging Protocol (ICMP) and TCP ping.
By default, Nmap will use ICMP to detect whether the host Off target or not. Network monitoring system used to keep records (logs) each event and the gateway device, such as firewalls, traffic stop ICMP. This can be neutralize by switching off the ping sweeps or by using other methods used by the firewall.
The process involves TCP Ping TCP Acknowledge (ACK) or packet synchronization (SYN) to a specific port on the target host. By default Nmap uses port 80, which is also used by the protocol Hypertext Transfer Protocol (HTTP), although it can also use other ports. Depending on the complexity gateway, network traffic that there can not be detected and finally in stop.
Port scanning to determine what TCP port can be used to communicate. This is very useful to explore the status of a network system computer for these ports represent the communication channels potential and mapping of these ports and facilitate exchange of information between host one with another host.
There are many techniques used to find out all the activities of data in a network. All the existing techniques involve searching information differ from each other between the operating system and then writes the results difference. Prove using FIN technique is one technique which is used by Nmap. It works by sending FIN packet or a packet without an ACK or a SYN signal to an open port in target computer and wait for a response from the target computer. Replies from target computer is a very useful information for parties perform scanning using nmap it. Information obtained include: a list of computer / host which is active in the network, a list of ports and its status on the target computer, the operating system used on the target computer, what services are running on the target computer. All such information is basic information and the potential can be used by the user to perform the next action to the target computer or computer network systems while being scanned. Such action may be to such good purpose for the sake of good network management by network administration, or for the benefit of an audit of the implementation security in computer networks, in addition to the things that benefit above, the information generated by nmap can also be used for the purposes is negative. Users who are not interested (hacker) can be used potential information as a basis for an active attack which is more dangerous to the network or computer system such targets. The process to obtain confidential information of a computer network system through a tool like Nmap by a hacker can be categorized types of passive attacks (passive attack).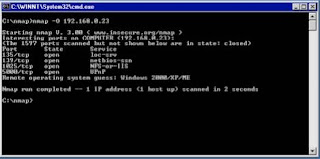
Conclusion
Nmap is one tool that is usually used to help a network administrator job in conducting oversight of the conditions that manages network security. Nmap includes a free software and can be downloaded freely and used by the GNU General Public License (GPL). Nmap network security side, including tools that can be used to attack a computer network system.
This tool is often used by a cyber hacker (hackers) to conduct information searches on a target computer prior to the attack on the target computer. The information generated by nmap status information includes a list of active computers in the network, the status of ports located on the target computer, type of operating system used, type of services available in the target computer, as well as security methods that are applied to the computer target if any. Activities to get information about the current state of the target computer can be categorized into types of passive attacks (passive attack). Where this type of attack does not harm a computer system is attacked, but the result of this activity was a hacker (hacker) can do to stage attacks on the attack to a target computer by using the information generated from the process of passive attacks that use tools like nmap. In addition to helping a network administration and even misused by hackers to perform a passive attack to a target computer, Nmap is also useful for security audit activities of a computer network by a Network Security Auditor. By looking at the information generated by nmap a security auditor can see whether the target computer in the audit are relatively safe or not can be determined so that appropriate security methods to the target computer. Read more...Routing Protocols and Concepts, CCNA Exploration Companion Guide
Sunday, November 15, 2009
Attack Tools for System Security and Computer Network Security Audit
By using the fingerprint technique TCP / IP is right and good, can be known What operating system being used by a target computer. In picture above, Nmap scans found that the target computer is scanned using Microsoft Windows 2000, Windows XP, or Windows ME.
Labels:
Computer Networking,
Tutorial Networking













0 comments:
Post a Comment
Please leave your message here..